New research on malware that set the stage for megabreach at the IT vendor SolarWinds shows that perpetrators spent months inside the company’s software development labs refining their attack before inserting malicious code in updates that SolarWinds sent to thousands of customers. More worryingly, the research suggests that the insidious methods used by attackers to subvert the company’s software development pipeline could be reused against many other major software vendors.
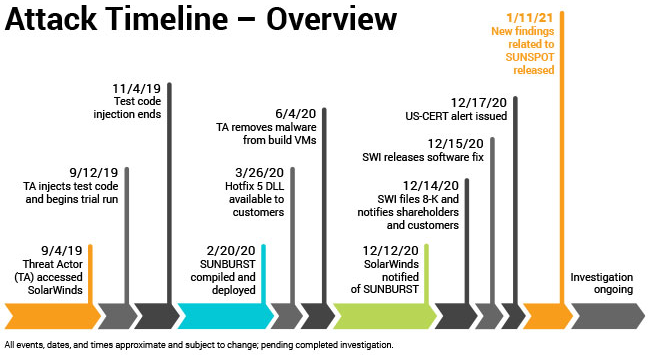
In a blog post published on January 11, SolarWinds said that attackers compromised their development environment for the first time on September 4, 2019. Soon after, attackers began testing code designed to surreptitiously inject backdoors into Orion, a set of tools used by many Fortune 500 companies and a wide range of the federal government to manage their internal networks.

Image: SolarWinds.
According to SolarWinds and a technical analysis of CrowdStrike, the intruders were trying to find out if their “Sunspot”Malware – designed specifically for use in undermining the SolarWinds software development process – can successfully insert your“shiny”Backdoor on Orion products without triggering any alarm or alerting Orion developers.
In October 2019, SolarWinds released an update for its Orion customers that contained the modified test code. In February 2020, attackers used Sunspot to inject the Sunburst backdoor into Orion’s source code, which was digitally signed by the company and propagated to customers through the SolarWinds software update process.
Crowdstrike said that Sunspot was written to be able to detect when it was installed on a SolarWinds developer system and to wait until Orion-specific source files are accessed by the developers. This allowed attackers to “replace source code files during the construction process, before compilation,” wrote Crowdstrike.
Attackers also included safeguards to prevent backdoor lines of code from appearing in the Orion software build logs and checks to ensure that such a breach would not cause build errors.
“The design of the SUNSPOT suggests [the malware] developers have put a lot of effort into ensuring that the code is inserted correctly and remains undetected, and has prioritized operational security to avoid revealing its presence in the building environment to SolarWinds developers, ”wrote CrowdStrike.
A third strain of malware – dubbed “Tear” in FireEye, the company that first publicized the attack on SolarWinds in December – was installed via Orion updates on networks that SolarWinds attackers wanted to loot more deeply.
So far, Teardrop malware has been found on several government networks, including the Commerce, Energy and Treasury departments, the Department of Justice and the U.S. Courts’ Administrative Office.
SolarWinds emphasized that, while the Sunspot code was specifically designed to compromise the integrity of its software development process, that same process is likely to be common throughout the software industry.
“Our concern is that even now similar processes may exist in software development environments at other companies around the world,” said SolarWinds CEO Sudhakar Ramakrishna. “The gravity and complexity of this attack has taught us that the most effective fight against similar attacks in the future will require an industry-wide approach, as well as public-private partnerships that take advantage of the skills, insights, knowledge and resources of all constituents.”

Tags: CrowdStrike, FireEye, Orion, SolarWinds violation, Sudhakar Ramakrishna, Sunburst malware, Sunspot malware, Teardrop malware
This entry was posted on Tuesday, January 12th, 2021 at 3:50 pm and is filed under Others. You can follow any comments to this entry through the RSS 2.0 feed. You can skip to the end and leave a comment. Pinging is currently not allowed.