A framework known for providing a banking Trojan horse has been redesigned to deploy a broader range of malware, including payloads of ransomware.
“The Gootkit malware family has been around for more than half a decade – a mature Trojan horse with functionality centered on stealing bank credentials,” said Sophos researchers, Gabor Szappanos and Andrew Brandt, in an article published today.
“In recent years, almost as much effort has been made to improve its delivery method as NodeJS-based malware itself.”
Called “Gootloader”, the expanded malware delivery system comes amid an increase in the number of infections targeting users in France, Germany, South Korea and the United States
First documented in 2014, Gootkit is a Javascript-based malware platform capable of performing a number of covert activities, including web injection, key capture, screen captures, video recording, as well as e-mail theft and password.
Over the years, the cybercrime tool has evolved to gain new information theft features, with the Gootkit loader adapted in combination with REvil / Sodinokibi ransomware infections reported last year.
While campaigns that use social engineering tricks to deliver malicious payloads cost a dime a dozen, the Gootloader takes that to the next level.
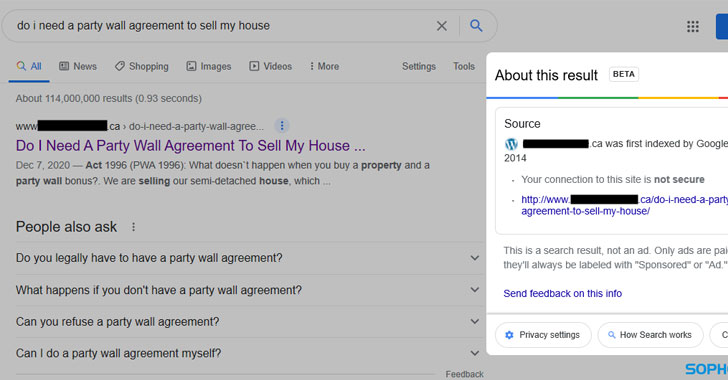
The chain of infection uses sophisticated techniques that involve hosting malicious ZIP files on websites belonging to legitimate companies that have been tricked into appearing among the top results of a search query using manipulated search engine optimization (SEO) methods.

Furthermore, the search engine results point to sites that have no “logical” connection to the search query, which implies that attackers must be in possession of a vast network of hacked sites. In a case detected by the researchers, advice for a real estate contract brought up a violated neonatal medical practice based in Canada as the first result.
“To ensure that targets from the correct geographies are captured, opponents rewrite the site code ‘on the go’ so that site visitors who are outside the desired countries see benign web content, while those in the right place see a page with a fake discussion forum on the topic they consulted, “said the researchers.
Clicking on the search result takes the user to a fake page similar to a message board that corresponds not only to the search terms used in the initial query, but also includes a link to the ZIP file, which contains a heavily obfuscated Javascript file which initiates the next stage of commitment to inject the fileless malware obtained from a remote server into memory.
This takes the form of an evasive multistage approach that starts with a .NET loader, which comprises a Delphi-based malware loader, which in turn contains the final payload in encrypted form.
In addition to delivering the REvil ransomware and the Gootkit trojan, several campaigns have now been seen taking advantage of the Gootloader framework to sneak Kronos financial malware in Germany and the Cobalt Strike post-exploitation tool in the U.S.
It is still unclear how operators gain access to websites to serve malicious injectors, but researchers suspect that attackers may have obtained passwords by installing Gootkit malware or by buying stolen credentials from clandestine markets or by taking advantage of security flaws present in the plug -ins used in conjunction with content management system (CMS) software.
The findings were repeated by Microsoft in a series of tweets, noting that it is “seeing several extensive manual attacks emanating from the Gootkit malware, which is distributed via drive-by downloads as JavaScript within a ZIP file.”
“The developers behind the Gootkit appear to have transferred resources and energy from delivering their own financial malware to creating a complex and stealthy delivery platform for all types of payloads, including the REvil ransomware,” said Gabor Szappanos, director Sophos Threat Research.
“This shows that criminals tend to reuse their proven solutions instead of developing new delivery mechanisms. In addition, instead of actively attacking endpoint tools as some malware distributors do, the creators of Gootloader have opted for complicated evasive techniques that hide the end result, “he added.