Hackers who target thousands of organizations worldwide in a massive phishing campaign have forgotten to protect their loot and left Google stolen passwords for public searches.
The phishing campaign has been running for more than half a year and uses dozens of domains that host the phishing pages. He received constant updates to make fraudulent Microsoft Office 365 login requests more realistic.
Creds in plain sight
Despite relying on simple techniques, the campaign was successful in circumventing email protection filters and collected at least 1,000 login credentials for corporate Office 365 accounts.
Researchers at cyber security companies Check Point and Otorio who analyze this campaign found that hackers exposed stolen credentials to the public Internet.
In a report published today, they explain that the attackers exfiltrated the information for domains that they registered specifically for the task. Their mistake was placing the data in a publicly visible file that Google indexed.
As a result, Google can show results for queries for a stolen email address or password, as seen in the screenshot below:

Researchers at the two cybersecurity companies say the attackers have also compromised legitimate WordPress servers to host the malicious PHP page delivered to the victims.
“Attackers generally prefer to use compromised servers rather than their own infrastructure because of the well-known reputation of existing sites,” explain the researchers.
By processing information from about 500 entries, the researchers were able to determine that companies in the construction, energy and IT sectors were the most common targets of these phishing attacks.

Simple and effective phishing
Attackers used several phishing email themes to lure potential victims into loading the landing page that collected their Microsoft Office 365 username and password.
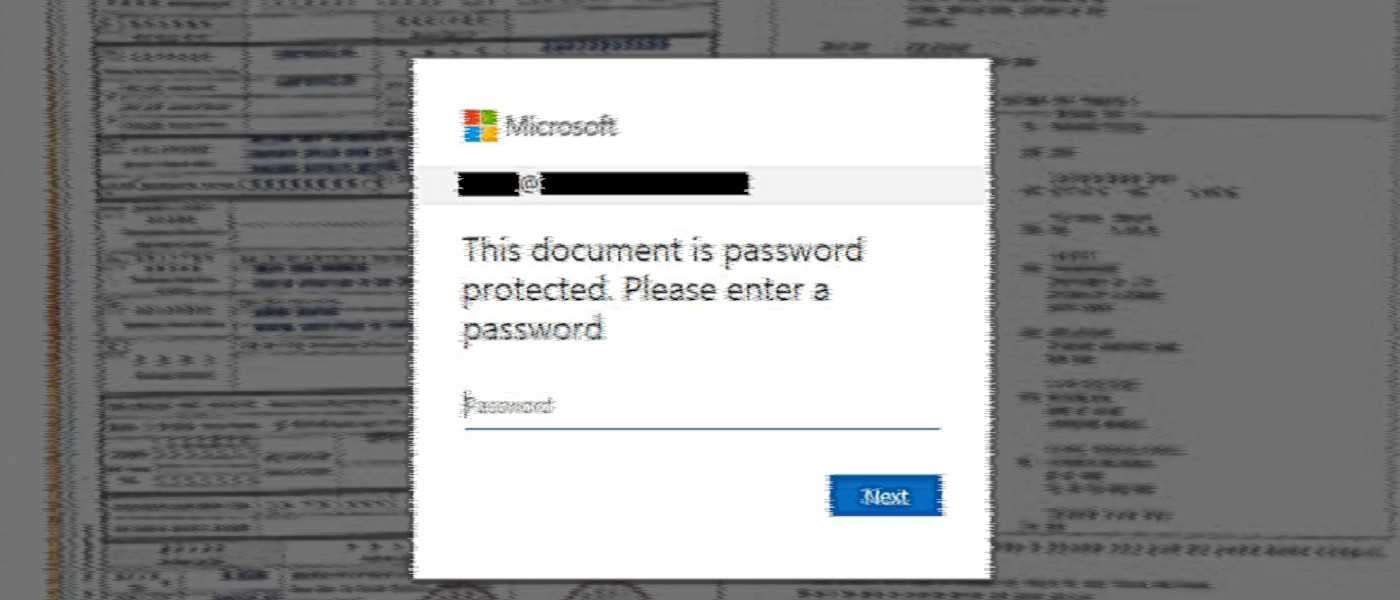
Malicious emails had the target’s first name or company title in the subject line and were intended to deliver a Xerox scan notification in HTML format.

Opening the attachment loaded in the standard web browser, a blurred image overlaid by a fake Microsoft Office 365 login form. The username field is already filled in with the victim’s email address, which normally removes the suspicion login theft.

JavaScript code running in the background checks the credentials for validity, sends them to the attacker’s drop zone server, and redirects the victim to the legitimate Office 365 login page as a distraction.

To keep the campaign undetected, the actor used compromised email accounts to distribute the fraudulent messages. For an attack, they impersonated the German hosting provider IONOS by 1 and 1.
Although this campaign started in August, the researchers found phishing emails from the same threat actor dated May 2020.
Although Google’s indexing of hacker pages, where they save stolen data, is not new, it shows that not all malicious agents are sufficiently qualified to protect their operations. Even if they are not identified, at least their actions can be frustrated.